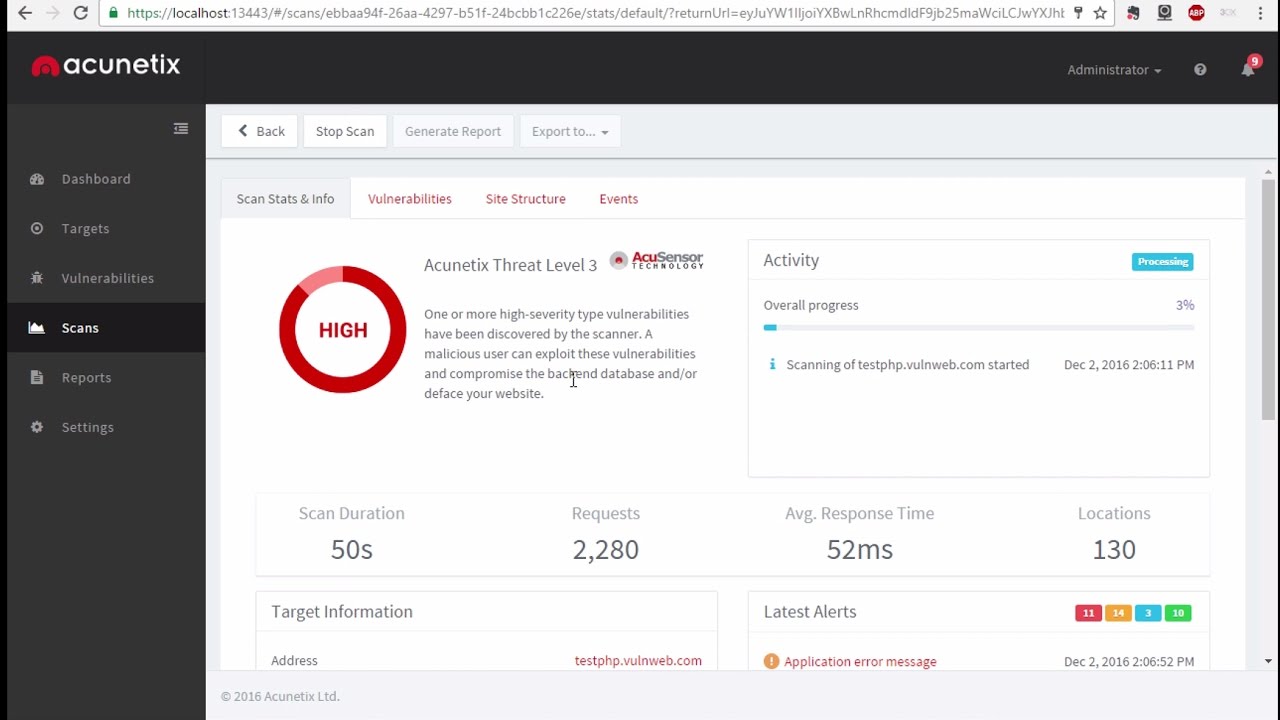
Aport scanis a method for determining which ports on a network are open. As ports on a computer are the place where information is sent and received, port scanning is analogous to knocking on doors to see if someone is home. It is also valuable for testing network security and the strength of the system's firewall.
Due to this functionality, it is also a popular reconnaissance tool for attackers seeking a weak point of access to break into a computer. The attacker sends a SYN request to the target port over TCP. The scanner then terminates the session without establishing a connection. If the port is closed, it responds with an RST packet, indicating that it cannot be accessed. If the port is located behind a firewall, the request does not generate a response at all. This is the most common scanning method because it does not require an established connection and is not logged by most simple event-tracking tools.
On the other hand, SYN scanning requires superuser privileges on the device that sends the requests and which might not belong to the attacker. Also known as filtered or dropped, this involves neither acknowledging the request nor sending a reply. No response indicates to the port scanner that a firewall likely filtered the request packet, that the port is blocked or that there is no port there. For example, if a port is blocked or in stealth mode, a firewall will not respond to the port scanner. Interestingly, blocked ports violate TCP/IP rules of conduct, and therefore, a firewall has to suppress the computer's closed port replies. Security teams may even find that the corporate firewall has not blocked all the network ports.
For example, if port 113, used by Identification Protocol, is completely blocked, connections to some remote internet servers, such as Internet Relay Chat, may be delayed or denied altogether. For this reason, many firewall rules set port 113 to closed instead of blocking it completely. A port scan is a series of messages sent by someone to learn which computer network services a given computer provides. Port scanners are applications that identify which ports and services are open or closed on an internet-connected device. A port scanner can send a connection request to the target computer on all 65,536 ports and record which ports respond and how. The types of responses received from the ports indicate whether they are in use or not.
This tool can test open ports, but it can also conduct a full recon of your network, assisting you in the identification of any potential security risks. An open port scanner tool or open port check tool can only afford you a small, limited picture of your network, system, and processes. That's why Engineer's Toolset also features an IP network browser. With the port scanner, this utility will sweep IP ranges, identifying devices, UDP and TCP services. This will afford you visibility of what services are reachable and which devices are connected to the network.
A port scanner is an application designed to probe a server or host for open ports. Such an application may be used by administrators to verify security policies of their networks and by attackers to identify network services running on a host and exploit vulnerabilities. All forms of port scanning rely on the assumption that the targeted host is compliant with RFC Transmission Control Protocol. This is especially true for less common scan techniques that are OS-dependent .
The TCP/IP stack fingerprinting method also relies on these types of different network responses from a specific stimulus to guess the type of the operating system the host is running. The website pentest-tools.com offers two port scanners based on nmap. The TCP scan claims to scan 100 common ports but in my testing it only scanned 21 ports. The UDP scan does not say what it does and in my testing, I have never been able to get it to work.
The big issue for me has been that it Pings before it scans and any router I configure blocks Pings. There is supposed to be a scan that does not require Ping, but it does not work. This is a limited free demo for a paid service that costs at least $55/month. These cybercriminals often use port scanning as a preliminary step when targeting networks. They use the port scan to scope out the security levels of various organizations and determine who has a strong firewall and who may have a vulnerable server or network. The goal behind port and network scanning is to identify the organization of IP addresses, hosts, and ports to properly determine open or vulnerable server locations and diagnose security levels.
Both network and port scanning can reveal the presence of security measures in place such as a firewall between the server and the user's device. Nmap is a utility for network exploration or security auditing. It supports ping scanning , many port scanning techniques, version detection , and TCP/IP fingerprinting . Nmap also offers flexible target and port specification, decoy/stealth scanning, sunRPC scanning, and more. Most Unix and Windows platforms are supported in both GUI and commandline modes. Several popular handheld devices are also supported, including the Sharp Zaurus and the iPAQ.
Rather than using the operating system's network functions, the port scanner generates raw IP packets itself, and monitors for responses. This scan type is also known as "half-open scanning", because it never actually opens a full TCP connection. If the target port is open, it will respond with a SYN-ACK packet. The scanner host responds with an RST packet, closing the connection before the handshake is completed.
If the port is closed but unfiltered, the target will instantly respond with an RST packet. To reduce scan time, do not run full UDP port scans unless it is necessary. UDP port scanning generally takes longer than TCP port scanning because UDP is a "connectionless" protocol. In a UDP scan, the application interprets non-response from the asset as an indication that a port is open or filtered, which slows the process.
When configured to perform UDP scanning, the application matches the packet exchange pace of the target asset. Oracle Solaris only responds to 2 UDP packet failures per second as a rate limiting feature, so this scanning in this environment can be very slow in some cases. Is used to determine what ports a system may be listening on. This will help an attacker to determine what services may be running on the system.
Some port scanners scan through ports in numeric order; some use a random order. There are many different methods used for port scanning, including SYN scanning, ACK scanning, and FIN scanning. In fact, the host discovery element in network scanning is often the first step used by attackers before they execute an attack. An alternative approach is to send application-specific UDP packets, hoping to generate an application layer response. For example, sending a DNS query to port 53 will result in a response, if a DNS server is present. This method is much more reliable at identifying open ports.
However, it is limited to scanning ports for which an application specific probe packet is available. Some tools (e.g., nmap) generally have probes for less than 20 UDP services, while some commercial tools have as many as 70. In some cases, a service may be listening on the port, but configured not to respond to the particular probe packet.
Adversaries may attempt to get a listing of services running on remote hosts, including those that may be vulnerable to remote software exploitation. Methods to acquire this information include port scans and vulnerability scans using tools that are brought onto a system. It is impossible to prevent the act of port scanning; anyone can select an IP address and scan it for open ports. To properly protect an enterprise network, security teams should find out what attackers would discover during a port scan of their network by running their own scan. Be aware, however, that security assessments and pen tests against many cloud hosting services, such as AWS, need approval prior to scanning.
Most security appliances can link ongoing repeated scan attempts from the same source whether they target a single host or multiple hosts. To be effective, port scan attacks may need to probe many different ports on many different systems over a relatively short time period, which makes the attempts easier to detect. To counter this, some attackers may find it preferable to probe for open ports over a much longer time frame, in which case it becomes more difficult to detect a port scan attack. The downside for the attacker, however, is that it may take hours, days or longer to find a vulnerable system. Port scanning is one of the most popular information-gathering methods used by malicious actors. Part of the reconnaissance process, an attacker can use the data collected by a port scan to find out what services a device is running and to get an idea of the OS being used.
This data can then be used to flag vulnerable systems with the intention of exploiting them to gain access to the network. When the target asset is on a local system segment , the scan occurs more rapidly because the asset will respond that ports are closed. The difficulty occurs when the device is behind a firewall, which consumes packets so that they do not return to the Scan Engine. In this case the application will wait the maximum time between port scans. TCP port scanning can exceed five hours, especially if it includes full-port scans of 65K ports.
The most common type of scan is a SYN scan , named for the TCP SYN flag, which appears in the TCP connection sequence or handshake. This type of scan begins by sending a SYN packet to a destination port. The target receives the SYN packet and responds with a SYN/ACK response if the port is open or an RST if the port is closed.
This is typical behavior of most scans; a packet is sent, the return is analyzed, and a determination is made about the state of the system or port. SYN scans are relatively fast and relatively stealthy, because a full handshake is not made. Because the TCP handshake did not complete, the service on the target does not see a full connection and will usually not log.
If Nmap receives an ICMP unreachable error it will report the port as filtered. These advanced port scanning options are stealthy and may bypass firewalls and other security controls. However, most host- and network-based intrusion detection systems will detect this type of scan activity. Keep in mind that OSes that don't follow the TCP RFC may send misleading responses. Businesses can also use the port scanning technique to send packets to specific ports and analyze responses for any potential vulnerability.
They can then use tools like IP scanning, network mapper , and Netcat to ensure their network and systems are secure. Use of vulnerability scanner tools, like AVDS, are standard practice for the discovery of this vulnerability. The primary failure of VA in finding this vulnerability is related to setting the proper scope and frequency of network scans. It is vital that the broadest range of hosts possible are scanned and that scanning is done frequently.
Your existing port scanner solution or set of test tools should make this not just possible, but easy and affordable. By sending a specially-crafted SNMP SetRequest PDU sent to UDP port 16, a remote attacker could exploit this vulnerability to cause the application to crash. It can detect the presence of security devices like firewalls etc. Generally, the port scanning process makes use of TCP and UDP protocols. Scans that are developed for the sender to go undetected by a receiving system's log are known as stealth scans and are of particular interest to attackers.
Despite its popularity in this area, port scanning is a valuable tool for fingerprinting a network and for a penetration tester to assess the strength of network security. UDP scanning is also possible, although there are technical challenges. UDP is a connectionless protocol so there is no equivalent to a TCP SYN packet. However, if a UDP packet is sent to a port that is not open, the system will respond with an ICMP port unreachable message. Most UDP port scanners use this scanning method, and use the absence of a response to infer that a port is open.
However, if a port is blocked by a firewall, this method will falsely report that the port is open. If the port unreachable message is blocked, all ports will appear open. The use of raw networking has several advantages, giving the scanner full control of the packets sent and the timeout for responses, and allowing detailed reporting of the responses. There is debate over which scan is less intrusive on the target host. SYN scan has the advantage that the individual services never actually receive a connection.
However, the RST during the handshake can cause problems for some network stacks, in particular simple devices like printers. Normal, benign system and network events from legitimate remote service scanning may be uncommon, depending on the environment and how they are used. Legitimate open port and vulnerability scanning may be conducted within the environment and will need to be deconflicted with any detection capabilities developed. Network intrusion detection systems can also be used to identify scanning activity. Monitor for process use of the networks and inspect intra-network flows to detect port scans. Firewalls and intrusion detections systems should always be configured to spot and block unusual connection attempts and requests.
For example, after a port scan has been completed, attackers may launch a few probing attacks to validate earlier research or to gain additional information needed to finesse their main attack. Feeding abnormal activity into a SIEM system can provide real-time feedback and improve automated responses to events. An appliance performing a high level of logging can cause a DoS situation. A strained network infrastructure and exhausted file system resources are known problems with debug-level logging (i.e., logging everything).
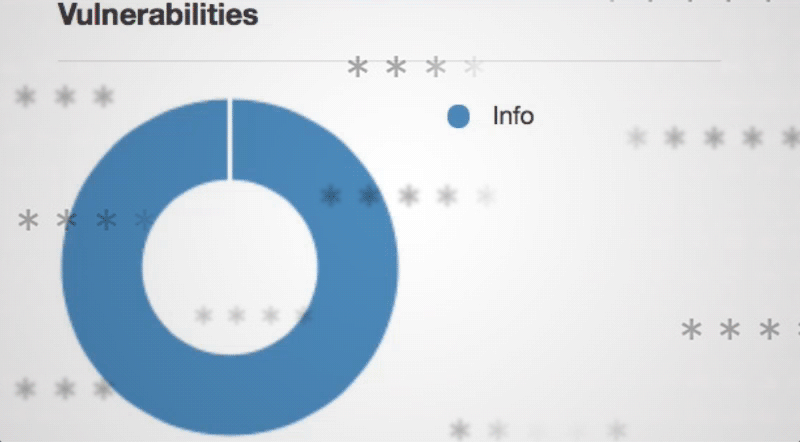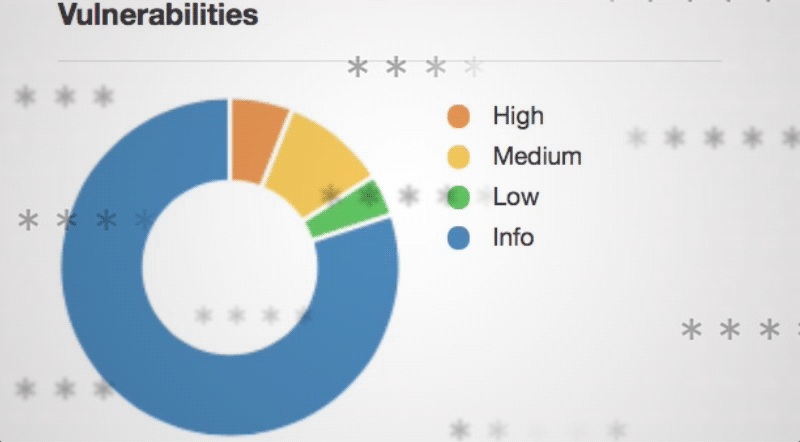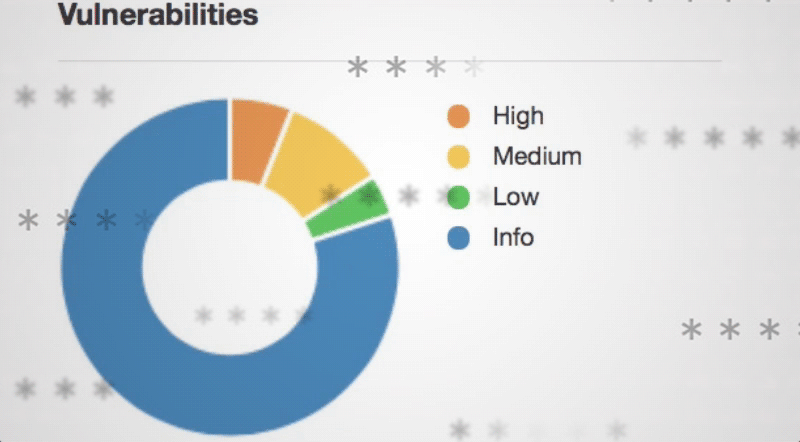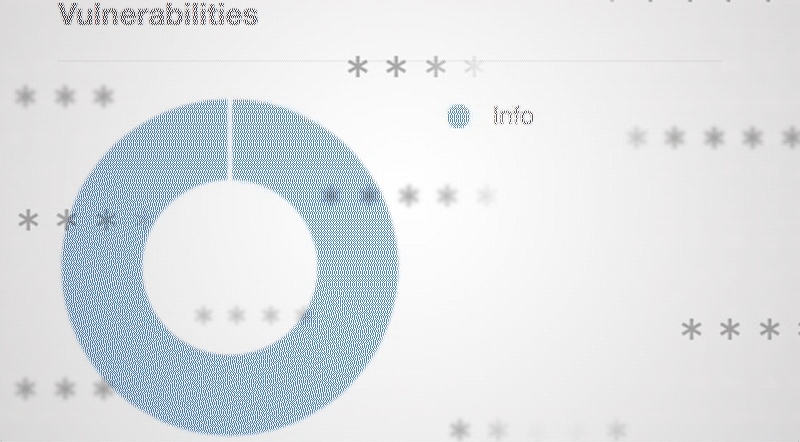
When a port scan is performed, the number of connections to a device can range from 1,500/3,000 ports connection attempts up to 65,535/131,070 ports connection attempts. Once the network scan has been scanned and a list of available hosts compiled, port scanner attack can identify the usage of specific ports. It will typically classify ports as open, closed, or filtered. RUCKUS could allow a remote attacker to bypass security restrictions. An unauthenticated remote attacker with network access to port 22 can tunnel random TCP traffic to other hosts on the network via Ruckus devices. A remote attacker could exploit this vulnerability to bypass security restrictions and gain unauthorized access to the vulnerable application.
As port scanning is an older technique, it requires security changes and up-to-date threat intelligence because protocols and security tools are evolving daily. One of the easiest ways for cybercriminals to gain access to an organization's devices is through open ports. System administrators and security professionals run port scans as part of vulnerability scans to identify such open ports and avoid any kind of intrusion.
In this blog, we'll take a deep dive into the various aspects of port scanning and the role it plays in vulnerability scanning. ManageEngine OpUtils' port scanner helps to secure the network by scanning and blocking ports running unauthorized services. It is a web-based, cross platform tool that runs on both Windows and Linux. OpUtils also offers IP address management and switch port mapping.
Now let's conclude the above tutorial, in this tutorial you learned how to write a Python script to check the Port vulnerability. You can look out for more vulnerable ports banners or services in google and add them in your txt file for a better result. A port scan or portscan is a process that sends client requests to a range of server port addresses on a host, with the goal of finding an active port; this is not a nefarious process in and of itself.